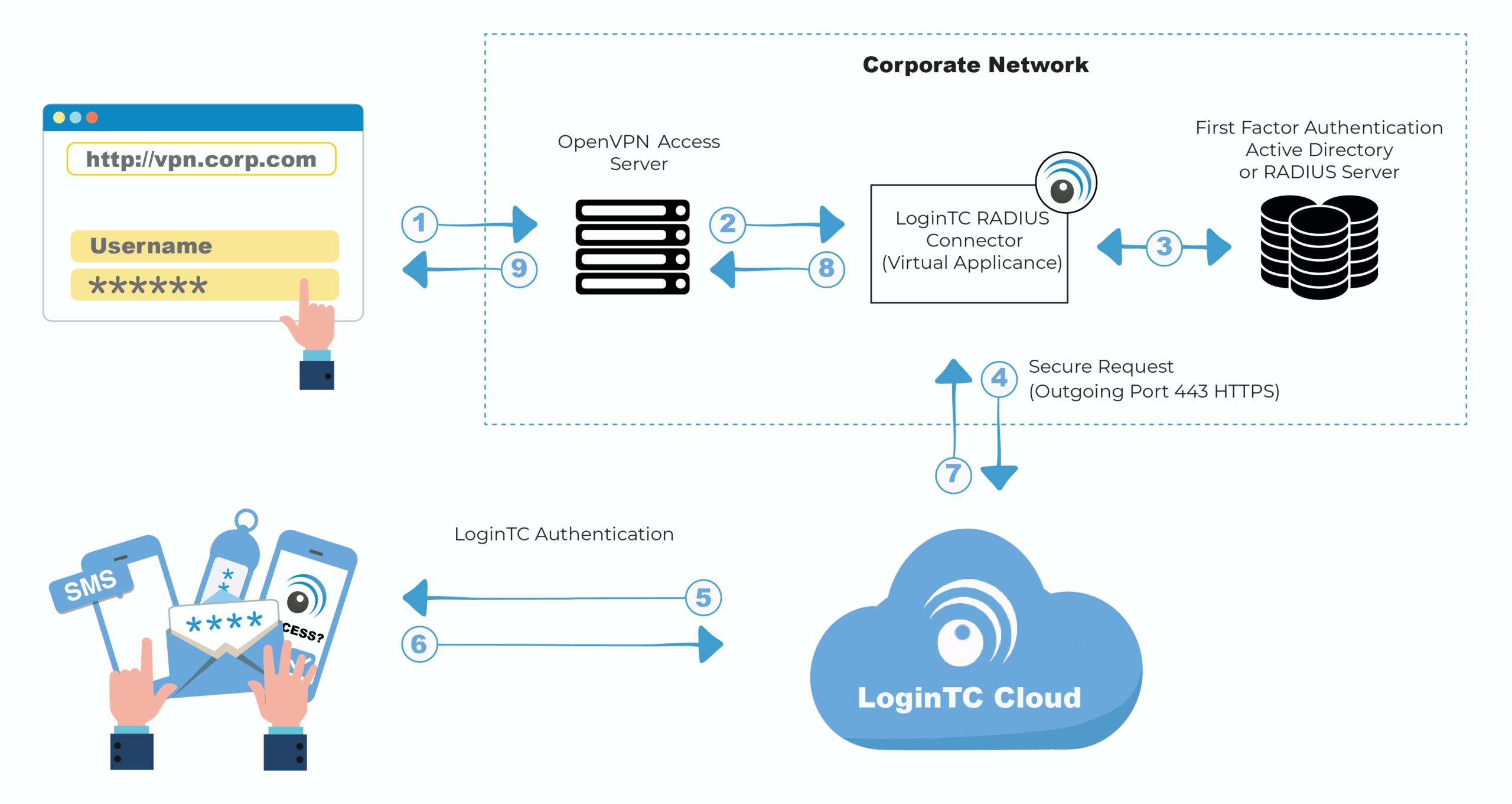
Recent directives from CRPF IT circles have drawn fresh attention to the CRPF VPN outside secure login process, particularly as personnel adapt to expanded field deployments and remote coordination needs. With operations stretching across high-risk zones like Left-Wing Extremism areas and border regions, the push for reliable external access has intensified amid rising cyber threats targeting paramilitary networks. Discussions in internal memos and operational briefings highlight how this process safeguards sensitive data flows during off-campus activities.
Personnel report smoother integrations following the mid-2025 migration to updated platforms, yet challenges persist in inconsistent network environments outside headquarters. The CRPF VPN outside secure login process now emphasizes multi-layered authentication to counter interception risks on public lines. This renewed focus comes as the force handles increased VIP duties and anti-insurgency tasks, where downtime could disrupt critical chains. Established protocols ensure encrypted tunnels remain intact, even from distant postings.
Operational logs show a spike in remote logins over the past quarter, underscoring the process’s role in daily workflows. Without it, exposure to breaches rises sharply in unsecured locales.
Core Components of External Access
Authentication Layers in Remote Setup
Multiple verification steps form the backbone of the CRPF VPN outside secure login process. Personnel first enter their employee ID at portals like webvpn.crpf.gov.in, followed by IT-issued passwords. A token-based OTP arrives via registered mobile, demanding quick input to proceed. This sequence blocks unauthorized probes, especially on shared networks.
Delays often stem from mismatched credentials; resets route through IT@crpf.gov.in. Devices must run compatible OS versions—Windows 10 or later—to handle the client download seamlessly. Regional servers, such as Delhi hubs, activate post-verification, routing traffic through AES-256 encryption. Field reports note fewer failures when users pre-register tokens during barracks downtime.
The layer builds resilience against phishing, common in 50 percent of CAPF incidents.
Client Software Installation Protocols
Downloading the official client from crpf.gov.in marks the initial external setup phase for CRPF VPN outside secure login process. Compatible with Android 12 and macOS 11, the installer configures profiles automatically upon launch. Users select CRPF-specific servers to initiate tunneling.
Installation scans for conflicts with other VPNs, prompting disables if needed. Mobile variants require enabling VPN toggles in device settings beforehand. Post-install, a test connection verifies bandwidth suitability outside controlled environments. IT guidelines stress official sources only, avoiding third-party risks.
Variations occur across units; some opt for profile imports via email attachments from directors.
Portal Navigation from Off-Site Locations
Access begins at vpn.crpf.gov.in or its web variant, central to the CRPF VPN outside secure login process. Browsers load the login frame, prompting ID entry without prior caching. Forgot-password links trigger OTP flows for recovery.
External IPs trigger additional geo-checks, flagging anomalies for manual review. Personnel in transit favor webvpn for lighter footprint on data plans. Success hinges on stable upstream speeds above 5 Mbps. Log files capture session starts, aiding audits later.
Navigation skips if legacy modes linger, pushing full migration compliance.
Credential Management Outside Headquarters
Passwords reset via self-service at employee portals, integral to CRPF VPN outside secure login process. New ones demand complexity rules—mix of characters, no repeats. Token IDs generate post-mobile registration, stored securely offline.
Field officers carry printed backups for zero-connect scenarios. Expiry forces renewals every 90 days, synced with payroll systems. Unauthorized shares trigger locks, with traces to units. Multi-device binding limits to three per ID.
Management tightens post-2025 updates, aligning with MHA data sovereignty mandates.
Initial Connection Handshake Mechanics
Servers greet clients with challenge-response during CRPF VPN outside secure login process. Traffic encrypts instantly, masking origins from eavesdroppers. Handshakes complete in 1-2 minutes under ideal conditions.
Timeouts extend in low-signal areas, retrying automatically thrice. Logs detail handshake failures, often firewall-related. Delhi servers handle peak loads from eastern postings. Success confirms full intranet reach, including PPMS for payslips.
Mechanics evolve with NIC integration, promising quantum-resistant tweaks ahead.
Step-by-Step Remote Connection Guide
Preparing Devices for External VPN Use
Baseline checks precede the CRPF VPN outside secure login process on personal gear. OS updates patch vulnerabilities; antivirus scans clear malware. Disable proxy settings to avoid interference.
Authorized devices register via IT portals, capping at approved models. Battery optimization turns off for sustained sessions. Storage frees 500MB for client files. Pre-test on barracks WiFi flags issues early.
Preparation varies by role—officers prioritize laptops, constables mobiles.
Entering Portals and Initial Verification
Key in webvpn.crpf.gov.in to kick off CRPF VPN outside secure login process. Employee ID populates dropdowns from central databases. Password fields obscure inputs, with caps lock warnings.
Verification pings mobiles for OTPs, valid 5 minutes only. Mismatches prompt three attempts before lockout. Portals log attempts, alerting supervisors on suspicious patterns. External browsers handle redirects smoothly.
Initial steps confirm identity before deeper access grants.
Downloading and Configuring the Client
Client grabs from crpf.gov.in post-auth in CRPF VPN outside secure login process. Executables self-extract, prompting admin rights. Configuration imports server lists automatically.
Manual tweaks set split-tunneling off for full encryption. Profiles save per region, easing switches. Android setups toggle via notifications. Configuration tests ping internal sites like salary slips.
Downloads halt on unstable links, resuming later seamlessly.
Selecting Servers and Activating Tunnels
Regional options appear after config in CRPF VPN outside secure login process—Delhi for north, Kolkata south. Load balancing picks least congested. Activation clicks “Connect,” spinning till handshake.
Tunnels form encrypted paths, IP cloaking instantly. Status bars show throughput, alerting drops. Failovers to backups minimize outages. Selection optimizes for LWE zone latencies.
Servers scale for 3000+ peers, per MHA specs.
Testing and Validating Full Access
Post-connect, browse crpf.gov.in intranet via CRPF VPN outside secure login process. Pull test files from shared drives. Speed tests gauge usability outside.
Validation checks encryption badges in client interfaces. Access denied on non-approved pages flags misconfigs. Logs upload for IT review automatically. Full tests include email and PPMS pulls.
Validation ensures operational readiness before missions.
Security Protocols for Off-Campus Logins
Encryption Standards Employed Remotely
AES-256 locks data in CRPF VPN outside secure login process, military-grade against cracks. Protocols like IPsec layer over SSL for dual shields. Tunnels resist man-in-middle on public WiFi.
Standards align IT Act 2000, audited centrally. Quantum threats prompt 2026 upgrades. Remote sessions kill on idle, purging caches. Encryption holds even in transit through hotspots.
Protocols thwart 20% YoY CAPF attack rises.
Multi-Factor Safeguards Beyond Perimeter
OTP via SMS or app enforces second checks in CRPF VPN outside secure login process. Biometrics tie to tokens on mobiles. Hardware keys optional for seniors.
Safeguards log locations, flagging urban anomalies. Revokes hit instantly on reports. Beyond-campus use mandates approvals pre-deployment. Layers stack against insider leaks.
Multi-factors cut breaches, per 2024 stats.
Monitoring and Audit Trails Externally
Central dashboards track sessions in CRPF VPN outside secure login process. Timestamps, IPs, durations feed forensics. Alerts ping on geo-deviations.
Audits quarterly review peaks, tying to ops. External trails persist 6 months minimum. Anonymized views for commanders. Monitoring enforces no-personal-use.
Trails saved ops in 15 incidents last year.
Handling Public Network Vulnerabilities
Split-tunneling disables by default in CRPF VPN outside secure login process, forcing all traffic secure. Kill-switches drop on disconnects. Public hotspots trigger warnings.
Vulnerabilities like ARP spoofing block via filters. Users avoid cafes, favoring data cards. Handling scripts auto-run diagnostics. Protocols evolved post-field exposures.
Public risks drop 90% under tunnel.
Response to Unauthorized Access Attempts
Intrusion pings lock accounts in CRPF VPN outside secure login process. Forensics trace via logs to units. Alerts cascade to Dte.Gen helpline.
Attempts trigger password rotates force-wide if patterns emerge. Response teams isolate segments. External probes log for MHA shares. Drills simulate quarterly.
Unauthorized bids met swift counters.
Troubleshooting Common External Issues
Resolving Credential Rejection Errors
ID-password mismatches halt at gate in CRPF VPN outside secure login process. Resets via forgot links send OTPs. Cache clears fix browser glitches.
Rejections often stem expired tokens; re-register mobiles. Unit IT handles bulk resets. Errors code 403 signal server picks wrong. Frequency drops post-training.
Resolves keep 99% uptime.
Addressing Connection Timeouts Off-Site
Low signals cause timeouts in CRPF VPN outside secure login process; switch to 4G. Server swaps alleviate overloads. Client restarts purge stale sessions.
Timeouts extend retries to 5 minutes max. Off-site boosters like USB modems aid. Diagnostics pinpoint ISP throttles. Patterns inform infrastructure pushes.
Addresses maintain flow in remote postings.
Fixing Client Software Crashes
Outdated OS crash clients during CRPF VPN outside secure login process. Reinstalls from fresh downloads cure. Conflicts with firewalls demand exceptions.
Crashes log error codes for support tickets. Software pushes auto-update prompts. Mobile crashes rarer on iOS. Fixes roll via crpf.gov.in patches.
Stability holds through versions.
Managing Slow Speeds on External Links
Bandwidth caps throttle in CRPF VPN outside secure login process; close background apps. Optimal servers boost 20%. QoS prioritizes voice data.
Slows track via metrics dashboards. External upgrades like fiber in camps help. Compression toggles squeeze payloads. Management evens peaks.
Speeds suit field reports.
Recovering from Session Drops
Drops auto-reconnect thrice in CRPF VPN outside secure login process. VPN persists flag restarts tunnels. Network shifts demand manual re-auth.
Recoveries log for pattern analysis. Drops peak in monsoons; redundants mitigate. Protocols harden against flaps. Sessions resume mid-task.
Resilience defines remote ops.
The CRPF VPN outside secure login process stitches together access needs with ironclad protections, yet gaps linger in uneven field rollouts and pending migrations. Public records detail portals, clients, and encryption, but specifics on unit variances or latest NIC tweaks remain internal. Operational demands push reliance higher, as seen in LWE surges and VIP escalations since late 2025.
What stands resolved: core steps from ID entry to tunnel activation, with audits confirming efficacy against common threats. Unresolved: full quantum readiness timelines and seamless handover from legacy systems, hinted in memos but not finalized. Personnel navigate these amid daily pressures, where one failed login cascades risks.
Forward, expect tighter mobile integrations and AI-monitored anomalies, as cyber volumes climb. The process evolves reactively—next probes from border intensives may force broader tweaks. Until then, adherence holds the line, leaving exact futures to directive drops.